You can’t go very long without hearing or reading something about a new ransomware attack. The term ransomware has forcefully entered our collective vocabularies over the last five years, and in that short time has become one of the most common and dangerous technology threats.
According to Verizon’s 2018 Data Breach Investigation Report, ransomware was the most common type of malware in attacks last year. But you don’t have to become a statistic. Here’s how you can prevent being added to ransomware’s growing list of victims.
Get TestRail FREE for 30 days!
What Is Ransomware?
Ransomware is one of the latest in a long list of software intended to operate in a malicious manner. This specially designed type of malicious software, commonly called malware, exists in many forms. Most people use the generic term virus to refer to most malware, but there are different types.
Many of today’s malware attacks are distributed as trojan horses, or just trojans. A trojan is software that appears to do something useful but actually unleashes an attack when the user runs it. Trojan designers try to either disguise their malware to look like another program, or just make it offer enticing features to encourage users to run it.
Trojans work so well because they rely on the curiosity or trusting nature of users to run the programs. When an attacker tricks a user into running the malware, it runs as a valid, authorized user. The victim carries out the bulk of the actual attack. Most ransomware attacks are distributed using trojans. Users have to take some action, such as clicking on a link in an email message or opening an attachment, to launch the ransomware attack. Once launched, the ransomware takes control of valuable files and makes them unavailable.
Different ransomware variants use different techniques, but one of the more common ways to take data hostage is to encrypt it. The attack code encrypts files using a key that only the attacker knows. More sophisticated ransomware generates a key that is unique to each victim. After files are encrypted, the software alerts the user and demands a ransom — hence the name — in exchange for the decryption key. The most popular payment method is via bitcoin. Ransom amounts vary but are generally higher for businesses and organizations.
Ransomware attackers set the ransom high enough to make the attack profitable but low enough to be cheaper than what the user would pay for recovery. According to Symantec’s Internet Security Threat Report, the average ransom demand fell last year to $522., but businesses can still face demands in the tens or hundreds of thousands of dollars.
How to Avoid Ransomware
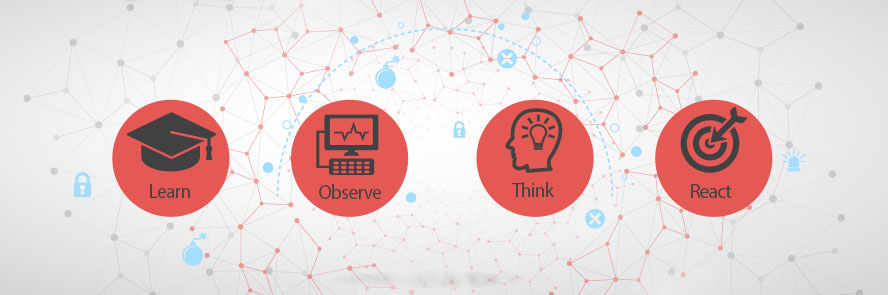
Responding to any known threat is all about preparation. There are four main steps that every individual and organization should take to prepare for a potential ransomware attack.
- Learn: Become aware of how ransomware attacks are launched and how they can succeed.
- Observe: Use your knowledge of ransomware attacks to monitor your environment for suspicious activity.
- Think: Change your online behavior to consider the impact before opening or accessing external technical resources such as attachments, links and images.
- React: Recognize an attack once it starts and know how to respond decisively and quickly.
There are lots of online resources to help deal with ransomware. CSO has a good article on ransomware prevention, protection and recovery for organizations. It discusses multiple technical controls to protect environments. Computerworld UK also published an article about responding to a ransomware attack. It is also oriented toward organizations and boils the process down to six basic steps.
The reason many of the latest articles focus on businesses and other larger organizations is that ransomware attackers have figured out that the money to be made attacking individuals isn’t as plentiful as it used to be. Businesses and organizations have more to lose as a result of an attack, and they often have a budget for handling such issues. Further, there is a cost associated with downtime. Individuals don’t always equate downtime with a loss of income, so they are becoming more willing to just work through the problem and not pay the ransom.
Even though individuals aren’t being targeted as much as in prior years, the threat is still very real. One of the most effective steps to prevent a ransomware attack is to recognize how the attacks work and do your best to deny an opportunity for attack. That means carefully considering every external resource before accessing it. Never open email attachments unless you trust the source and expect the attachment. The same applies to social media. Never click on any link unless you trust its origin. When in doubt, type in any link manually.
Tripwire has a solid list of 22 ransomware prevention tips that provides a starting point for thwarting attacks. Their first suggestion is to create and maintain current backups. That is always good advice. Having good backups of the files you really need makes you more able to face any disaster or loss. In fact, most of the tips in this article make you safer in general.
Join 34,000 subscribers and receive carefully researched and popular article on software testing and QA. Top resources on becoming a better tester, learning new tools and building a team.

What to Do After a Ransomware Attack
In spite of the best intentions, sometimes attackers succeed. What do you do if you find that you have become a victim of a ransomware attack? The answer depends on how seriously you prepared for such an attack.
Try this exercise. Turn off your computer or mobile device. Pretend that it was unexpectedly infected with ransomware. You now have no access to that device. Can you still conduct your business as usual? What do you do?
That is what suffering a ransomware attack is like. You simply do not have access to your computer or mobile device anymore. If you took the previous section to heart, you should have current backups available to you so that you can reload your computer or device, restore your files, and be back up and running in a matter of hours in most cases.
However, if you didn’t prepare, your list of options is pretty short. IBM publishes a Ransomware Response Guide that can help businesses respond to attacks.
But as an individual, if you’re lucky, you could have been hit with ransomware that is weak and has been broken. For example, researchers recently released a new decryptor tool for the Everbe ransomware. Kapersky and Trend Micro also have tools that will help decrypt some ransomware, and an internet search for “ransomware decryptor” will return many other sites as well. Of course, make sure that you trust any tools you choose to download.
Otherwise, you only have two real options to recover from a ransomware attack: pay the ransom (Don’t do this! It only emboldens the attackers), or lose your data and start over.
Of course, the best defense is a good offense. Be prepared. It can save a lot of money, time and hassle.
Article written by Michael Solomon PhD CISSP PMP CISM, Professor of Information Systems Security and Information Technology at University of the Cumberlands.
Test Automation – Anywhere, Anytime