In today’s interconnected world, certain sectors operate under strict regulatory requirements designed to uphold standards of safety, security, and compliance. These industries, often referred to as regulated industries, encompass sectors such as healthcare, finance, pharmaceuticals, and energy, among others. Within these sectors, protecting data integrity and privacy isn’t just a matter of good practice—it’s a legal and ethical imperative.
Regulated industries are subject to a myriad of laws, regulations, and standards aimed at safeguarding sensitive information, ensuring consumer protection, and maintaining trust in critical systems and services.
From the Health Insurance Portability and Accountability Act (HIPAA) in healthcare to the Sarbanes-Oxley Act (SOX) in finance, these regulations dictate stringent requirements for data handling, storage, and transmission.
Testing software in an environment resembling production is crucial for ensuring stability and maintaining compliance. Yet, in sectors like banking or healthcare, where data sensitivity is high, testing poses security risks.
Fortunately, methods exist to test systems without compromising sensitive data.
Understanding the importance of data integrity and privacy in regulated industries is crucial. Compliance is vital for legal adherence and maintaining stakeholders’ trust and confidence.
Challenges in regulated industries
Organizations operating within regulated industries face unique challenges in maintaining data integrity, ensuring privacy, and achieving regulatory compliance. Let’s explore these challenges and the corresponding solutions to address them effectively.
| Challenges | Solutions |
| Difficulty in testing software with sensitive data | Utilize property-based testing to generate realistic data for testing without using or storing actual production data |
| Ensuring compliance while testing software with production data | Implement data de-identification and masking techniques, follow regulatory guidelines such as HIPAA Safe Harbor and Expert Determination |
| Handling multiple configurations of test data | Implement test data parameterization to run the same test with multiple configurations of different values |
| Maintaining high test coverage with minimal duplication of test creation efforts | Utilize centralized test management tools like TestRail Enterprise with built-in test data parameterization capabilities to create and manage test cases efficiently |
Now that we’ve covered some of the main challenges in regulated industries let’s explore the vital role of data de-identification and masking, property-based testing, and test data parameterization in safeguarding sensitive information, validating software behavior, and streamlining testing processes in regulated environments.
Data de-identification and masking
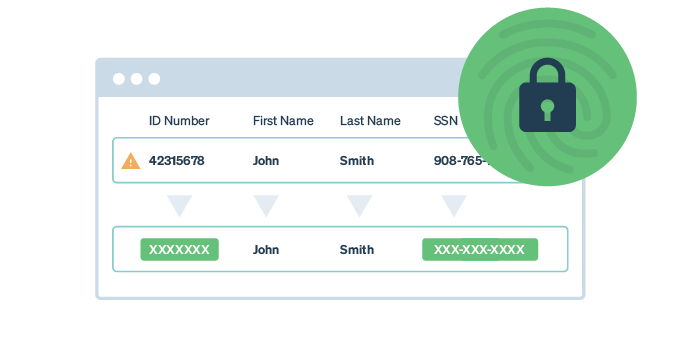
Data de-identification and masking are essential techniques regulated industries employ to protect sensitive information while enabling effective testing and analysis. These processes involve altering data in such a way that it cannot be directly linked to the individuals it represents. By removing, replacing, or obscuring personal identifiers dictated by regulatory bodies or risk-based statistical analysis, organizations can mitigate the risk of unauthorized access or disclosure of sensitive data.
Methods and tools for implementation
Data de-identification plays a crucial role in healthcare, where compliance with regulations like HIPAA is paramount. HIPAA expressly governs data de-identification, making many of the available tools and resources relevant to the healthcare industry. However, the benefits of data de-identification extend beyond healthcare and are applicable to any industry that needs to sever its test data from the identities of its original subjects.
HIPAA outlines two primary methods for data de-identification: Safe Harbor and Expert Determination.
Safe Harbor mandates the removal of eighteen specific categories of information from datasets. These eighteen elements for de-identification include:
- Names
- All geographic subdivisions smaller than a State
- All elements of dates (except year) for dates directly related to an individual
- Telephone numbers
- Fax numbers
- Electronic mail addresses
- Social security numbers
- Medical record numbers
- Health plan beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers and serial numbers, including license plate numbers
- Device identifiers and serial numbers
- Web Universal Resource Locators (URLs)
- Internet Protocol (IP) address numbers
- Biometric identifiers, including finger and voice prints
- Full-face photographic images and any comparable images; and
- Any other unique identifying number, characteristic, or code except as permitted by the re-identification rules
While Safe Harbor ensures compliance, removing critical information may render the dataset less useful for analytical purposes.
Alternatively, Expert Determination allows organizations to retain certain identifiers if an expert determines the risk of identifying individuals from the data is sufficiently low. This risk-based approach provides flexibility while still upholding privacy standards.
Numerous tools and platforms are available to assist organizations in effectively implementing data de-identification and ensuring compliance with regulatory requirements while safeguarding sensitive information. Learn more about the landscape of data de-identification tools on G2.
Importance of compliance and data privacy
Compliance with regulations such as HIPAA is non-negotiable for organizations operating in regulated industries. Ensuring data privacy not only protects individuals’ sensitive information but also fosters trust and credibility among stakeholders.
By adopting robust data de-identification and masking techniques, organizations can confidently conduct testing and analysis without compromising individuals’ privacy or violating regulatory mandates. These practices demonstrate a commitment to ethical data handling and bolster the organization’s reputation within the industry.
Property-based testing
Software reliability and integrity are crucial in industries subject to strict regulations. Property-based testing offers a robust method for thoroughly validating software behavior while adhering to regulatory standards.
What is property-based testing?
Property-based testing uses a specialized tool to dynamically generate realistic data to test the property of a given field without using or storing any actual production data.
Additionally, property-based testing can quickly test an immense range of inputs in a single test—making it easy to check for edge cases without having to write a different unit test for every potential input.
Key advantages
One of the primary advantages of property-based testing is its ability to efficiently validate software properties without relying on actual production data. By automating the generation of test cases/test data or both depending on the tool, property-based testing accelerates the testing process and improves the detection of subtle bugs and vulnerabilities.
Popular libraries and tools
Several libraries and tools facilitate property-based testing across different programming languages and platforms:
- Faker (JavaScript): Faker provides developers with a versatile toolkit for generating realistic fake data, making it ideal for property-based testing in JavaScript applications.
- Hypothesis (Python): Hypothesis stands out as a powerful property-based testing library for Python, offering seamless integration with existing test frameworks and advanced data generation capabilities.
- RapidCheck (C++): RapidCheck empowers C++ developers with automatic test case generation based on user-defined properties, enabling comprehensive testing of C++ codebases with minimal effort.
- ScalaCheck (Scala): ScalaCheck leverages Scala’s expressive features to facilitate property-based testing in Scala applications, ensuring robustness and reliability.
Benefits for regulated industries
In regulated industries such as healthcare and finance, property-based testing enables organizations to validate critical software components while adhering to strict compliance requirements. By automating the generation of test data and scenarios, property-based testing reduces the reliance on sensitive production data, mitigating privacy and security risks.
By incorporating property-based testing into their testing strategy, organizations can enhance the robustness and reliability of their software systems. This proactive approach allows developers to identify and address potential issues early in the development lifecycle, leading to improved software quality and increased confidence in critical systems.
Test data parameterization
If property-based testing isn’t the right fit for your requirements and you find yourself with a library of de-identified data values for testing, what’s the solution? When the prospect of crafting individual unit tests for each input field and data value becomes overwhelming, test data parameterization offers a solution to streamline the process.
With test data parameterization, you can run the same test with multiple configurations of different values. This data-driven testing method enables testing of the same underlying logic or functionality in your application with multiple inputs, eliminating the need for duplicating and managing multiple test cases.
Image: Within TestRail Enterprise, you can run parameterized tests using test data, which allows testers to create test variables and datasets for their test cases and test runs.
For instance, TestRail Enterprise provides a built-in test data parameterization feature, empowering you to define up to 500 variables, such as input fields, and up to 100 different datasets for each variable. These variables can then be added to test cases, enabling a single test case to encompass all potential datasets associated with that variable.
This approach offers project-specific test data, granting substantial flexibility in constructing test cases and achieving broader coverage with fewer cases to oversee. For detailed guidance on leveraging this feature, refer to the TestRail Enterprise User Guide.
Utilizing test data parameterization in TestRail
TestRail facilitates test data parameterization through its built-in feature that allows users to define variables and datasets. Here’s how TestRail can help employ test data parameterization:
- Define variables: TestRail enables users to define up to 500 variables, such as input fields or parameters, within a project.
- Assign variables to test cases: Users can easily associate variables with test cases, allowing for flexibility in testing by covering multiple scenarios within a single test case.
Image: With TestRail Enterprise, you can add up to 500 variables to your test cases, enabling seamless integration of diverse data sets for comprehensive testing.
- Create datasets: For each variable, TestRail supports the creation of up to 100 different datasets. These datasets represent various configurations or values for the defined variables.
Image: Within TestRail Enterprise’s test data management area, you can add new test data values, view and edit existing data, and import or export test data via CSV.
- Greater test coverage: By leveraging test data parameterization in TestRail, organizations can achieve greater test coverage with fewer test cases to manage. This approach enhances efficiency while ensuring comprehensive testing of software functionality.
- Detailed documentation: TestRail provides comprehensive documentation and user guides to help users understand and effectively utilize the test data parameterization feature.
TestRail simplifies the process of test data parameterization, empowering organizations to efficiently manage test cases, improve test coverage, and ensure the reliability of their software systems.
Bottom line
In regulated industries, safeguarding data integrity, ensuring privacy, and maintaining compliance are non-negotiable. By employing strategies such as property-based testing, data de-identification, and test data parameterization, organizations can navigate regulatory complexities while upholding the highest standards of data protection and software reliability.
Ready to streamline your testing process and ensure compliance in regulated industries? Unlock the power of TestRail Enterprise’s features, including test data parameterization and robust test case management. Elevate your testing standards and enhance software reliability with TestRail. Get started with your free 14-day TestRail trial today!